In this post – we are going to create a quick ASA topology in GNS3 and have some fun with access lists basics.
Here is our topology – I will go ahead and configure OSPF everywhere so we have full reachability. I also placed X.X.X.X loopbacks on the devices that will be nice for testing purposes. I used 3.3.3.3 on the TestPC:
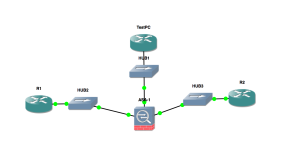 If you are wondering what those hubs are all about – I read somewhere that they are the least finicky when it comes to getting the ASA to speak to the devices on the network. I know direct connections and the Ethernet Switch in GNS3 are both buggy. I cannot wait for VIRL to feature the ASA in April 2015.
If you are wondering what those hubs are all about – I read somewhere that they are the least finicky when it comes to getting the ASA to speak to the devices on the network. I know direct connections and the Ethernet Switch in GNS3 are both buggy. I cannot wait for VIRL to feature the ASA in April 2015.
So we better start with a basic sanity check. Lets try and Telnet from the inside (R1) to the outside (R2). We expect this to work of course thanks to the inspection of TCP and UDP traffic by the ASA with its default rules in place:
R1#telnet 2.2.2.2
Trying 2.2.2.2 ... Open
User Access Verification
Password:
R2>
Well – that worked great – did the ASA inspect it? Let’s check:
ASA1# show conn detail
7 in use, 10 most used
...
TCP outside:2.2.2.2/23 inside:10.10.10.1/64631,
flags UIO, idle 57s, uptime 59s, timeout 1h0m, bytes 102
ASA1#
Yes indeed.
Now – let’s say we want R1 to be able to ping R2. This is not possible by default. Let’s punch a hole in the outside interface inbound so that ECHO-REPLY packets can make it for this specific ping.
access-list OUT_IN permit icmp host 192.168.1.1 host 10.10.10.1 echo-reply
access-group OUT_IN in interface outside
So I just did the ping on R1 (ping 192.168.1.1) and it worked perfectly, so that very specific access list did its job.
But wait a minute – didn’t we just break Telnet from the inside to the outside? That access list has an implicit deny all at the end…
I just tried a Telnet from R1 to R2 and it worked perfectly just as before. What gives?
Well – for those Reply packets for the Telnet from the inside, inspection happens first – then the ACL. So the traffic is indeed permitted in this case even with our outside access control list permitting the ping responses.
DO NOT CONFUSE ACCESS LISTS WITH INSPECTION. They are indeed two different things and it is very important to know each separately and how they operate – and then how they would react when combined.
Thanks for reading. We will take this topology and have even more fun with it in the next post.
