
Here is post on the SID in AD serving as a great primer for Identity in Windows Server 2016.
SID Overview
In our post here at the blog on the important FSMO roles, we examined the RID Master. This device helps with the creation of unique Security Identifiers (SIDs) in the domain. The SID is used to uniquely identify an object that receives security permissions. A SID consists of several components. One of those components is the Relative Identifier (RID). The RID Master gives your domain controllers each their own portion of the overall RID pool. This keeps different domain controllers from creating and assigning the same SID to different objects in your domain.
The SID Dissected
The Windows SID is generally made up of 2 fixed fields and up to 15 additional fields all separated by dashes. For example, the format looks like this:
S-v-id-s1-s2-s3-s4-s5-s6-s7-s8-s9-s10-s11-s12-s13-s14-s15
Here is the actual SID I am using right now on Windows 10:
S-1-5-21-863435222-3640012759-1033413245-1001
Notice the following about SIDs:
- The first fixed field (v) describes the version of the SID structure, Microsoft has never changed this from 1
- The second field (id) is the identifier authority; it uniquely identifies the authority involved; for example, NULL (0), World (1), Local (2), NT Authority (5)
- The next 15 fields are not all required and are called sub-authorities; they help uniquely identify the object
- The last sub-authority field is normally the RID
Well-Known SIDs
There are indeed well-known SIDs. For example:
- S-1-5-10; this represents NT Authority/Self
- S-1-1-0; this represents Everyone
There is also a well-known RID of 500. This translates to the built-in administrator account. Here we can see this on my Windows 10 system:
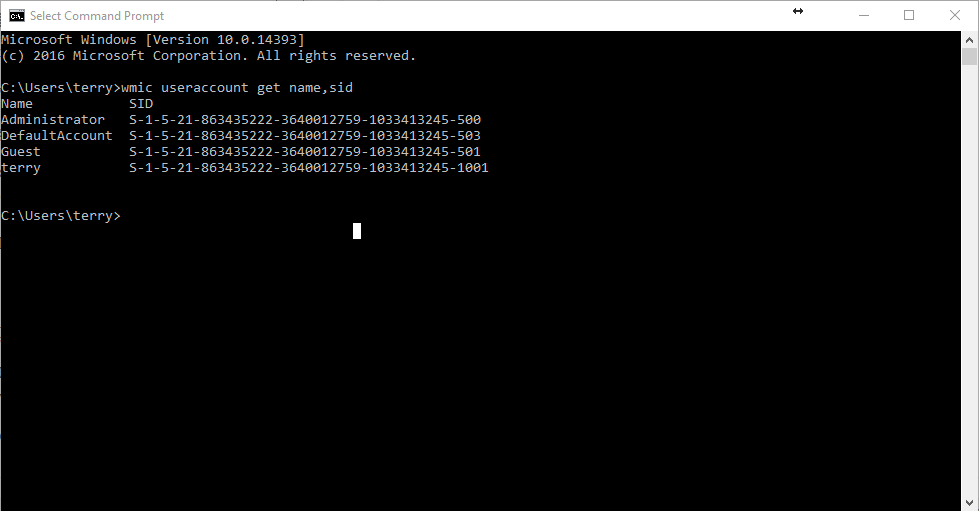
I hope you enjoyed this post on the important SIDs in Windows technologies!
All r using do no who that’s just fake person doing close all this plese
I think you are asking me if this content was generated by AI. The answer is NO.