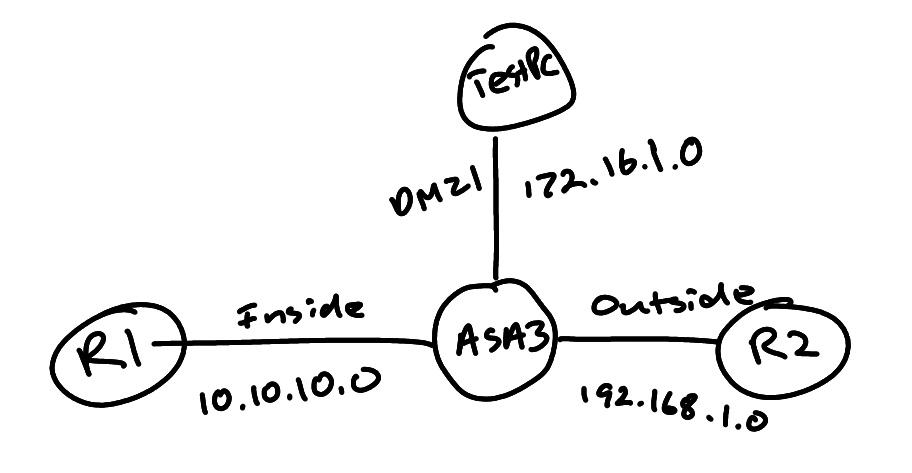
What if you are asked to use objects in access lists. Note we are saying objects here – not object groups. The big difference is that an object can only contain a single entity. Let’s take a look at a sample configuration. In fact – let’s allow a return ping from a device on the outside like we did in earlier access list posts, but this time, we will use objects. I am using real gear in this example since my crappy little GNS3 image does not support the use of objects, only object groups.
object network INSIDEHOST
host 10.10.10.1
object network OUTSIDEHOST
host 192.168.1.1
object service PINGREPLY
service icmp echo-reply
access-list OUT_IN permit object PINGREPLY object OUTSIDEHOST object INSIDEHOST
access-group OUT_IN in interface outside
Sure enough – this config worked great:
Rack4R1#ping 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
Rack4R1#
In fact – if you look at the access list – you see it is enumerated normally:
ASA3# show access-list
access-list cached ACL log flows: total 0, denied 0 (deny-flow-max 4096)
alert-interval 300
access-list OUT_IN; 1 elements; name hash: 0x16c2190a
access-list OUT_IN line 1 extended permit object PINGREPLY object OUTSIDEHOST object INSIDEHOST (hitcnt=0) 0x088a9534
access-list OUT_IN line 1 extended permit icmp host 192.168.1.1 host 10.10.10.1 echo-reply (hitcnt=1) 0x088a9534
ASA3#