There are so many variations that are possible with NAT now – and I am just talking in the “new rules”. In this post, lets just review one. We will do dynamic NAT with a PAT backup using network objects. We will provide the NAT instructions manually instead of inside an object.
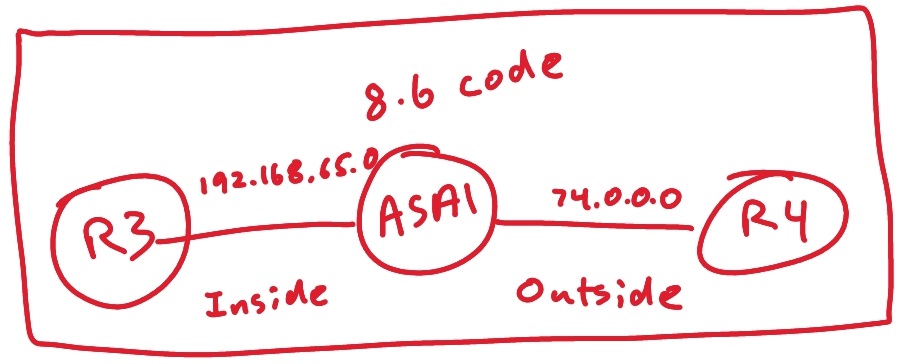
Our topology is as follows:
Our objective here is as follows:
- Configure NAT so that hosts on the inside network 192.168.65.0/24 attempting to reach the outside network are translated using the pool 74.0.0.102 to 103. We need to use the interface IP address as a PAT backup. The NAT configuration must be manual.
My first step is to create my network objects:
object network 192INSIDE subnet 192.168.65.0 255.255.255.0 object network POOL1 range 74.0.0.102 74.0.0.103
Verification of this step is show run object.
Now I am ready for the manual NAT:
nat (inside,outside) source dynamic 192INSIDE POOL1 interface
The above command is made VERY easy thanks to context-sensitive help.
For verification – we do not even need to leave the ASA thanks to Packet Tracer!
packet-tracer input inside tcp 192.168.65.3 1027 4.4.4.4 23
...
Phase: 4
Type: NAT
Subtype:
Result: ALLOW
Config:
nat (inside,outside) source dynamic 192INSIDE POOL1 interface
Additional Information:
Dynamic translate 192.168.65.3/1027 to 74.0.0.102/1027
...
Result:
input-interface: inside
input-status: up
input-line-status: up
output-interface: outside
output-status: up
output-line-status: up
Action: allow
ASA1#
Of course, we can always create traffic through the ASA and view the translation. Here I telnet through from R3 on the inside to R4 on the outside. We confirm out configuration and that traffic is matching it:
ASA1# show nat
Manual NAT Policies (Section 1)
1 (inside) to (outside) source dynamic 192INSIDE POOL1 interface
translate_hits = 6, untranslate_hits = 6
ASA1#
Of course I will be back with plenty of other “new” NAT sample configurations and verifications for you.